THE CHALLENGE
Our customer needed an automated DMaaS solution to secure and safely move massive volumes of highly sensitive data from on-premises servers to a cloud storage solution. They also wanted to ensure they could tokenize sensitive data and share it between different environments.
But their existing manual processes were insecure and time-consuming and put them at high risk for human error. Furthermore, they needed a solution that would comply with rigorous government regulations as well as company policies.
THE SOLUTION
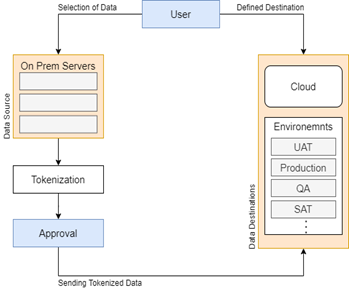
EveryIT implemented a full data movement as a service (DMaaS) solution for the customer. As part of the DMaaS solution, EveryIT secured sensitive data using tokenization and automated processes to quickly and securely move data to the cloud and different environments such as user acceptance testing, production, and quality assurance.
To ensure a highly secure and compliant solution that could handle massive data volumes, EveryIT first conducted an in-depth analysis of the customers’ business needs and existing environment and chose technologies that could fully meet project requirements.
EveryIT then designed a tokenization tool that requires only a handful of inputs, such as the data to be copied and the data destination. Once the inputs are specified, the tokenized data is automatically moved to its destination with a single click.
To further improve the security of the entire process, once the data is tokenized, it is scanned and sent to a manager for review and approval before the actual transfer. This approval process adds an extra layer of security and provides our customer with greater control over the data transfer process.
Diagram of the DMaaS solution
THE RESULTS
Thanks to the highly secure and automated DMaaS solution from EveryIT, our customer was able to reap multiple benefits. Benefits include:
- Ability to handle massive volumes of data quickly and efficiently.
- Secure end-to-end data transfer and management processes.
- Compliance with government regulations and company policies.
- Fewer hours required to manage the process.
- Headcount reduction from twelve to six.
- Elimination of manual processes and risk of human error.
TECHNOLOGIES USED
The solution uses the following technologies:
- Spring Boot Microservices
- React for the front-end design
- JWT for authorization, CBH, Pyspark and Scala for data processing
- Protegrity for tokenization
- Distcp for copying the data
